How are businesses and organisations handling your email? I know how they’re handling mine!
For about 10 years I’ve used “burnable email addresses”. These are email addresses that I can use and expire. They are unique to every relationship between me and another organisation, business or blog that I register with. This means I know who’s got my email and if they’ve leaked it. I know if they’ve shared if or if they’re spamming it.
I guess that makes me a living honeypot? But, unlike many automated honeypots that try to trap malicious users, the data from my email servers are based on real-world interactions between myself and others.
Below is a short summary of my findings from the last three years. It summarises my email interactions with 3rd parties in real-world situations.
Method for creating unique emails
Some email services have the ability to set up aliases, and others allow users to insert a token value in to their address; for example, gmail allows users to put a plus (+) after their email and create a unique address like basilsmiththethird+someblog@gmail.com and basilsmiththethird+forum@gmail.com. Unfortunately that’s pretty predictable and while handy, it’s easy for scammers and malware to strip off the unique token by removing anything between the + and the @.
My emails take a complicated form that would require a custom parser to be written, they include regular expressions and expected sequences embedded in the whole email name. For example an example address I create for Amazon could be: “sbetamazndtj15@my.domain”.
My unique email addresses are easy to reverse if you know the rules, but if you’re doing bulk spamming or emailing you probably wouldn’t go to the effort. My unique email addresses are also easy for me to generate in my head as I’m talking on the phone, filling in forms etc. This means I can give them to anyone at any time, online or in person.
Gathering the data
The data have been obtained organically. The living email honeypot is the result of my interactions with what I perceived to be legitimate individuals and organisations. In the last three years, I’ve created 139 identities, which are unique pairings of me and “someone else”.
Most identities are the result of: sign-ups to forums; software downloads; mailing lists; and e-commerce sites. I’ve unsubscribed and re-subscribed as appropriate, and haven’t gone out of my way to hide or attract the attention.
Simply, the data represents the results of all interactions I’ve had with 3rd parties except for interactions with friends and family.
Results overview
So, are my email identities well managed?
Overall, yes! Most organisations can be trusted to handle my email data appropriately.
Out of 139 unique relationships that I have developed within the last three years, only one has been seriously abused; most likely due to the business being hacked.
Key Points:
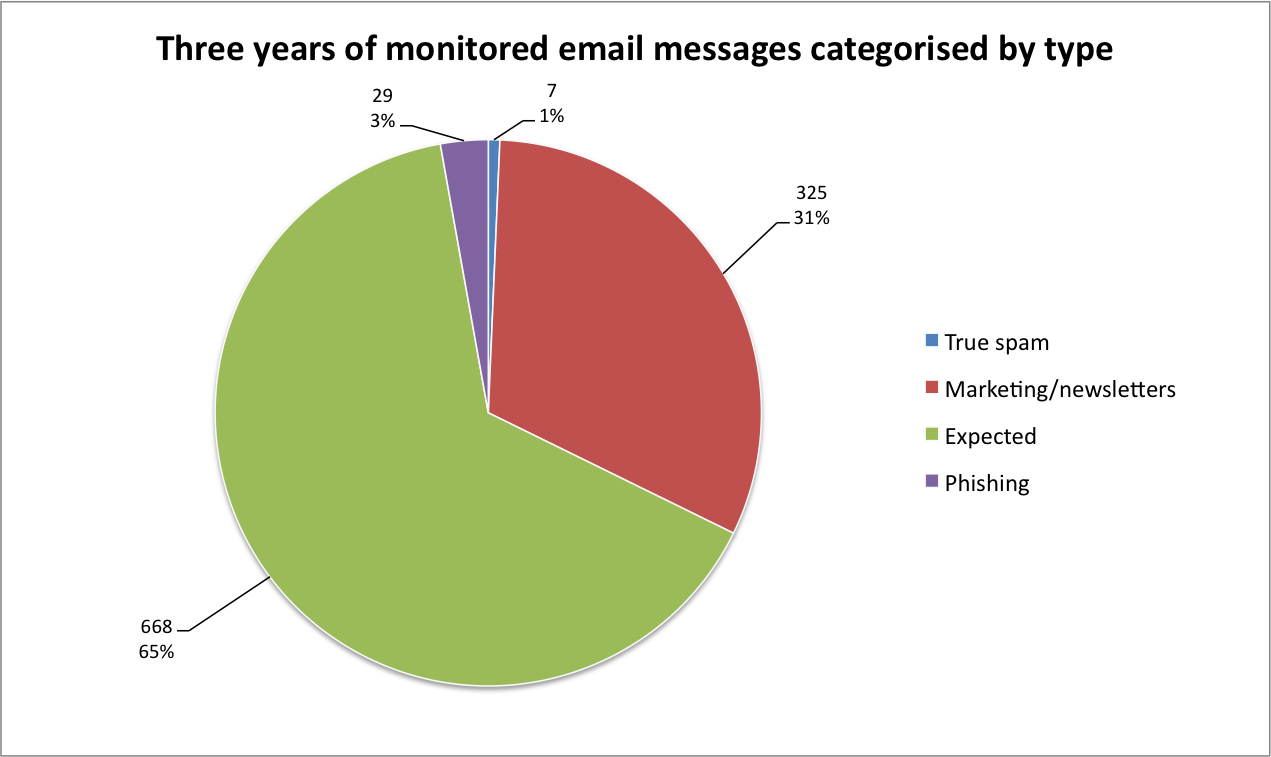
- 139 unique email addresses received 1029 emails between March 2013 and February 2016.
- 134 out of 139 organisations have appropriately managed my email information.
- 65% of emails were expected and provided the services subscribed to.
- 31% of emails consisted of marketing material in-line and expected based on the relationship I had with the organisation.
- Four identities have been shared with expected 3rd parties, which means the content that was served by the 3rd party is consistent with the services/support provided by the original party.
- One identity associated with a local small business was breached three years ago and still receives bulk phishing emails.
- Unsubscribing from legitimate email lists works and is usually pain-free!
The data indicate that businesses are generally responsible with their care and handling of customer email addresses.
Semi-solicited spam
Spam wise, I consider 31% of the content received by my living-honeypot expected spam. These emails are trying to sell me something, and even if I don’t want what they’re selling, the email is being sent to me in the context of our existing relationship. I don’t really have an issue with this; you can’t blame a business for trying.
I was also happy to see that almost all of the organisations that sent marketing emails provided functional un-subscribe links. They also managed their email lists in-house or through a recognised list distribution services.
Only four of my email identities were shared with related 3rd parties for the purposes of marketing. These are on the fringe of my comfort zone, but no further proliferation has occurred, so it appears the related parties are behaving appropriately too.
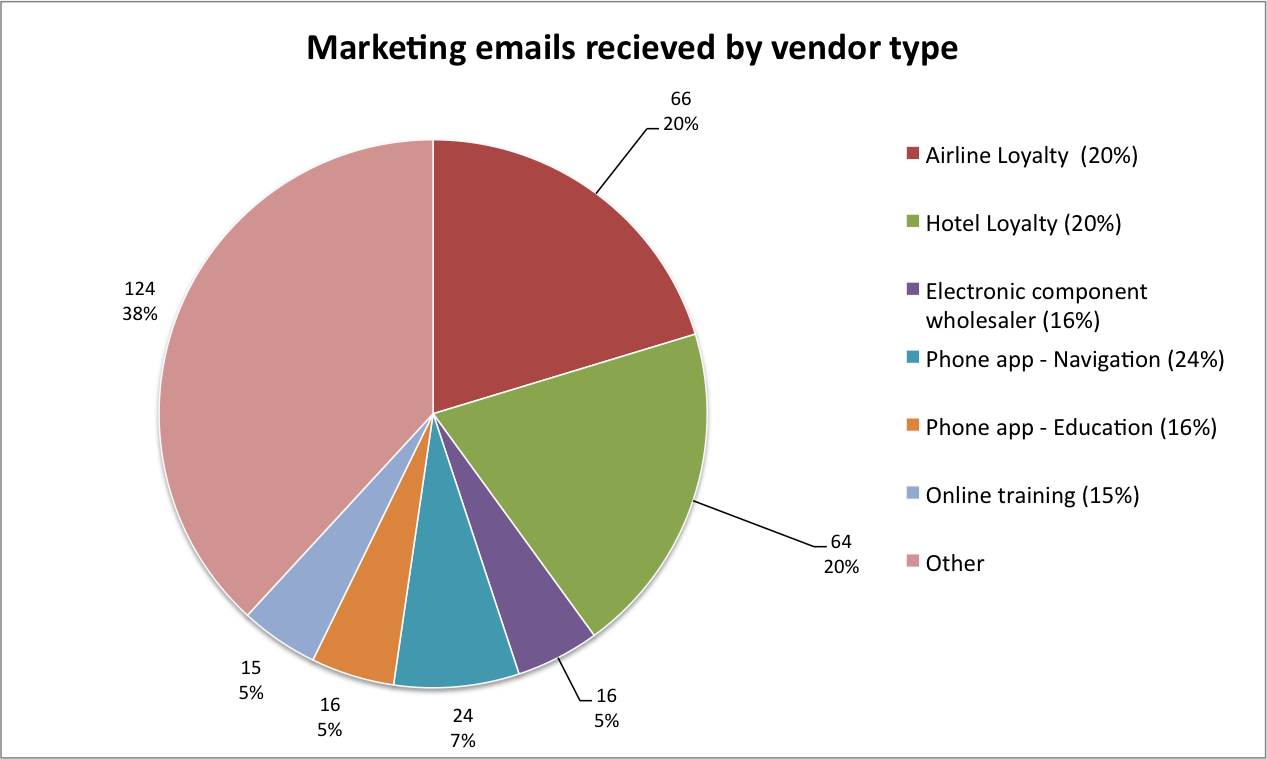
The bulk of marketing email spam came from a high-profile frequent flier program, two high-profile hotel loyalty clubs, mobile phone app ’logins’, and an online training provider. However, these were still in-line with the services and correspondence I expected to receive.
Unsubscribing
Unsubscribing from email lists and marketing works!
Some organisations signed my email up to several associated lists. For example, one business signed me up for: newsletters; product information; and special offers. Almost all organisations had an easy to access unsubscribe feature, and most had a bulk “un-subscribe from all lists” feature. A few organisations required each email list to be unsubscribed manually - a minor inconvenience.
One hotel loyalty club make it difficult to unsubscribe. They don’t provide an unsubscribe link and instead, provide instructions to log in to an account. Unfortunately, that login uses my membership number and I have no clue what that could be!
BUT…
There’s a big caveat on the unsubscribe button:
Do not click on any links in a malspam email. If you unsubscribe from a legitimate lists it works, but if you accidentalyl ‘unsubscribe’ from a spam or scam list, you are sending a ‘signal’ to the scammers that your email address is alive and monitored - you may also expose yourself to ‘one click’ malware.
If in doubt, don’t click (ever).
Malware and phishing on the breached email
One organisation (a local small business) stands out as serious concern. Their customer database appears to have been breached.
I bought $20 worth of product from a small business’ online store in early 2013. Three months after dealing with the business, their unique email identity started receiving phishing spam. The business was notified in 2013, and they took no action.
The clients of this business are also likely to be users “of all walks” including older folks (I’ve seen many retirees in their physical store). I’m assuming from my discussions with them, that many of their clients are not tech-savvy. Several of them are likely ideal targets for scammers.
The latest scam email received arrived yesterday (23 February 2016); a PayPal phishing link. I tested the link in a virtual machine, it was still active (24 hours after the message was received), and appeared to be running on a compromised small business website in Austria.

The phishing link also had multiple unique id passed to a script. It remains to be seen if that results in more spam (because now they know that email is real, and maybe I even look like a sucker).
Conclusion
Businesses and organisations are doing the right thing by their customers and users. Personal details aren’t being leaked en masse, and email marketing is consistent with the services of the business.
But it’s not all good news! One breached business has resulted in dangerous phishing and malware emails that continue several years after my last contact with them. It’s quite conceivable that their clients have have phished and the customers of that business don’t even know that their emails have been compromised.
From an end-user or customer point of view, you’re pretty safe with most organisations. If they seem reputable or want your details to provide you with a service, the data indicate that they do behave appropriately. However, remember data is forever; a business can be sold or hacked, possibly many years after you stop dealing with them.
Businesses will spam you to a degree. They’ll send you newsletters, marketing offers and reminders. Most of these are legitimate and easy to unsubscribe from; just make sure if you do unsubscribe, you’re only unsubscribing from genuine lists not from malware.
From a business point of view, it’s clear that even one breach is too many. Businesses rely on client data, mailing lists and communication; it’s essential that you keep everything safe and secure! Imagine the damage a breach could do to your brand if word got out?
Businesses should be continuously reviewing their cyber security and digital assets. You should be asking yourself: what IT and security policies do we have in place; who has access to our information; are we up-to-date with software and operating system patches; is our website secure?
Customer information needs to be treated with respect, most businesses seem to understand that risk and most are doing a good job. But, when things go wrong, they go really wrong.