Ransomware is profitable! The bad guys are achieving investment returns over 1500% with very low risk. With the right connections, anyone can acquire ransomware as a service; they could buy some ransomware & pay to spread it to users around the world.
What is ransomware?
Ransomware is a type of malware that affects your computer, blocks access to your personal data and demands a ransom payment to unlock your files. It’s also quite successful; imagine losing your data, documents, family photos or life’s work. How much would you have lost? How much would you pay?
Evolution
Two interesting developments in the history of ransomware have allowed us to analyse how it evolves:
- The first true ‘encrypting’ ransomware family - GPCode
- Incorporation of ‘dark networks’ and crypto currencies
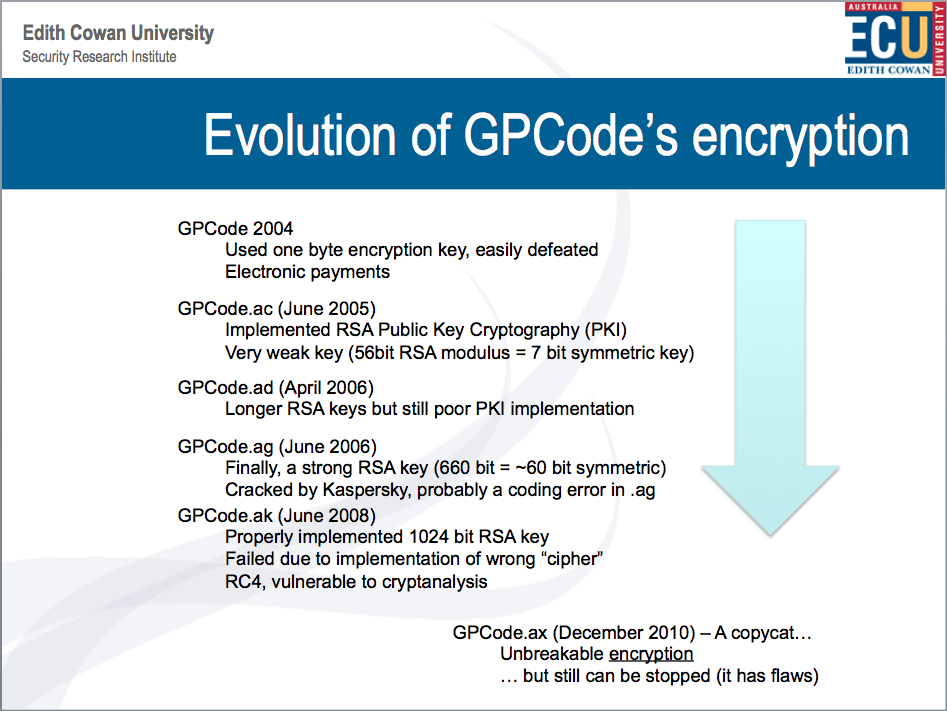
The GPCode ransomware first appeared in 2004. The developers used a homemade encryption scheme that was easily defeated by security experts. While the first variant of GPCode wasn’t particularly effective, what happened next changed the ransomware game.
GPCode started to evolve, the developers realised that implementing their own security didn’t work, so they implemented a well-known and secure encryption algorithm. They had learned from their previous mistakes and updated the software to fix bugs and shortcomings. GPCode continued to evolve and over the next six years it became more secure and eventually, it became impossible to break.
GPCode’s evolution showed that malware could be made to securely lock and ransom end-user data. It also showed other bad guys a how to make ‘better’ ransomware. GPCode provided a design pattern that future malware developers could use as a basis for their work.
New technology
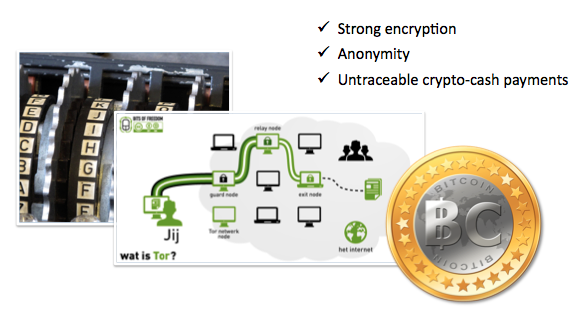
Until 2013 ransomware servers were frequently located and ‘taken down’. Financial transactions could also be traced, leaving a trail of evidence and made ‘cyber extortion’ more risky. In response, ransomware evolved again to use new technologies including hidden ‘dark’ networks and Bitcoin payments.
By adding these technologies, the bad guys could communicate anonymously; securely deploy and manage ransomware; demand payments; and receive funds without ever revealing their identity or relying on 3rd parties to process payments.
The future
Malware developers are pragmatic and are looking to profit from their work. To get an idea of where ransomware is headed we need to ask:
- Where are the opportunities (where is it failing)?
- Where’s the money?
Two large opportunities for development jump out at me. Firstly, end-users and businesses with solid backup regimes are currently protected. A user with recent backups can respond to a ransomware attack by restoring their important files from a backup, without paying.
Secondly, corporate database records remain largely untouched. Ransomware can easily identify user files, but databases often contain complex data and lots of it. Manipulating database records without early detection isn’t so easy.
The history of ransomware evolution suggests that (when it becomes profitable) new generations will evolve to leverage these opportunities. We can expect new variants of ransomware that lay-low to slowly locate and encrypt all backups. We will also see strains that attack database servers or entire disks.
Advice for now
Backup your data across several removable disks that you switch regularly. Don’t leave backup drives plugged in.
Keep your operating system and applications up to date. Don’t open dodgy attachments or visit unknown web sites.
If you think you’ve been compromised by ransomware, minimise data loss by powering off immediately by pulling the plug or battery - seek help!
0
READY.